Break into Cybersecurity - With or without Tech Background!
Get hands-on skills, expert mentorship and the confidence to launch or advance your career
Start your Cyber Journey today
Enrollment is ongoing
Secure Your Spot Now!




Join 150+ students who’ve gone from uncertain to expanding their potentials
Go from Zero tech experience to Cybersecurity Expert
time commitment
Mode
We are Accredited and Authorized
Training Partners With:






Does this sound like you?
Underpaid in your current role
Want a Higher-Paying, More Stable Career? You're tired of low pay or job uncertainty and want a career with strong demand, great earning potential, and growth opportunities.
Struggling with Job Applications & Interviews?
You’ve applied to cybersecurity jobs but rarely hear back—or feel unprepared when you do get an interview.
Feeling Stuck in Your Current Career?
You want to break into cybersecurity but feel overwhelmed by where to start or whether you have the right skills.
Lack of Funds & Time
Don’t let financial challenges hold you back! We offer flexible payment plans to make learning accessible and affordable.
Worried That AI Will Replace Your Job or Need a Remote Job?
With AI reshaping industries, you're concerned about job security and future career growth. You want a field that’s AI-proof, high-paying, and offers remote opportunities—but you’re unsure where to start
Just Like Oyin

Oyin was a stay at home mum with no technical degree and coding skills. After completing the training she was able to land two Cybersecurity offers.
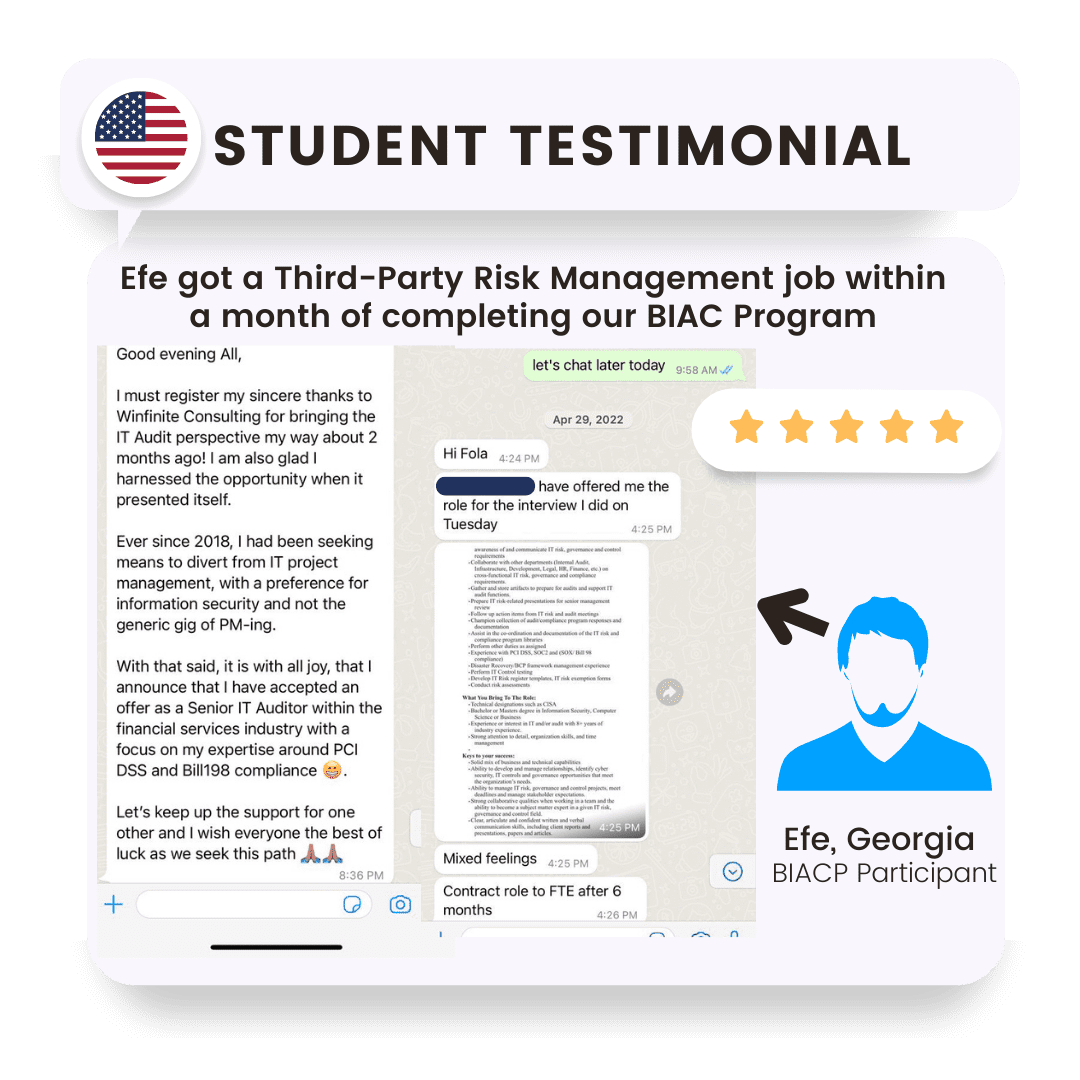
Look at Efe

She was an optometrist with no tech background but she managed to land $120,000/ year role. It goes on and on
Student Testimonials
Watch our FREE Training to learn how to kickstart a Cybersecurity Career with NO Tech Experience
Still have some questions or not sure you can successfully transition?
Watch the video now and take the first step towards securing your future cybersecurity career.
Where Our Students Work































Self-paced via our LMS or through Live Classes
3-6 months
land their first job
Your Dream Tech Career Starts Here
Tired of your dream tech career feeling like a distant fantasy? It’s time to turn that dream into reality with Winfinite. Your success is our inspiration. We are committed to equipping you with all the essential tools you need to secure and excel in your first Cybersecurity job like a true pro.
Choose Your Pathway to a New Career
Career Mentorship Packages
Our comprehensive consultations will delve deep into your skills, strengths, and growth areas, enabling us to craft a personalized plan designed specifically for your journey.
- 0 Lessons
Digital Cybersecurity Launchpad
Cybersecurity Program: Bundle Essential to Help Start and Advance Your Cybersecurity Career With No Prior IT Experience This comprehensive bundle…
- 0 Lessons
Cybersecurity GRC + AI Program
Our Cybersecurity Program (CSP) equips you with the skills to seamlessly pivot into Cybersecurity. It is an opportunity for you to launch a lucrative and...
- 18 Lessons
ISO/IEC 27001 Information Security Lead Auditor eLearning Course
The ISO/IEC 27001 Lead Auditor eLearning course will equip you with the skills needed to audit an Information Security Management…
- 0 Lessons
Why Our Students Have Exceptional Success Stories
Flexible & Interactive Classes
Live classes help you learn well with like minds, and Self-paced digital lessons allow you to learn at your own pace. You can access recorded live video sessions to catch up on any missed classes.
Industry-centric Curriculum & Expert Instructors
Our curriculum is structured to cover essential topics, taking you from a beginner to an expert. It includes career support services such as Job Search Strategy, Resume Revamp, Interview Prep & Personalized Career Roadmap.
Internship & Digital Community
Internship opportunity with a Tech Startup. Access to a private community of individuals with the same goals where you can ask questions and rub minds 24/7.
Post Training Support & Mentorship
Receive guidance from industry professionals beyond the program to apply your skills in real-world scenarios. Get access to Job opportunities and Referrals.

What Our Students Are Saying
"Thanks to Fola (Lead Coach) for all the amazing sessions she had with us. The way she delivered the lessons and walked us through the contents made me fall in love with the Cybersecurity space. Fola is SUPER AMAZING and I would say for sure the financial and time investment into getting knowledge from the Cohort is a wise investment."

Titi Showande
Cybersecurity LaunchPad Program AlumniThanks to Winfinite Consulting for bringing the Cybersecurity perspective my way! I'd been trying to transition from IT project management to Information Security and not the generic gig of PM-ing. With that said, it is with all joy, that I announce that I have accepted an offer as a Senior Cybersecurity Compliance Specialist within the financial services industry with a focus on my expertise in PCI DSS, SOX compliance and TPRM.

Efe A
If you are looking for a program that will help you break into Tech, look no further. The Cyber Launchpad program is a well thought-out and highly structured Cybersecurity program that will provide you with a solid foundation as you venture into the world of cybersecurity. The program's highly sought-after and knowledgeable instructor is an educator par excellence. I will recommend her services anytime any day. Kudos FOLA!

Julius A
USAFinally, I can give my review. Hi guys, taking this course has been my best decision. It has helped me navigate my career beyond my expectations. I got real value for my money. I got a job in one of the top 5 banks in Canada. I'm so happy This course is worth it, do the math. Imagine paying this small money and landing a job that pays *100. I am so proud of how @Fola is grooming us to reach for the stars. I highly recommend this Cybersecurity training as well as follow-ups (mentoring & interview prep)

Ola
Cyber Launchpad Alumni"I started this course with no prior knowledge or experience of cybersecurity and within 4 months, I passed my certification and started preparing for job interviews. Thank you, Fola!"

Babatunde Adekanmbi
Cybersecurity LaunchPad Alumni

What you will learn in the program
Lesson 1
Cybersecurity & AI Governance and Risk Management (including Third-Party Risk Management)
Lesson 2-3
Cybersecurity Standards & Frameworks (ISO27001, NIST CSF, 800-53, RMF, SOC 2, PCI-DSS, GDPR, FISMA, SOX, COBIT, HIPAA, CSA, etc.)
Lesson 4
Implementing Security Controls
Lesson 6-7
Security Control Assessment (Practical Data Analytics)
Lesson 8
Cybersecurity Infrastructure & Operations (Network Security, DRP, Patch & Vulnerability Management, Common Vulnerability Exposure, Security Incident Response Plan, Security Operations Center, etc.)
Lesson 9
Introduction to Penetration Testing (including code scanning)
Lesson 10
Practical Industry Case Studies, Career Development & Job Readiness (Job Search Strategy, Resume Building, Interview Preparation, Resume Clinic)
Lesson 11
Career Mapping, Building a Professional Cybersecurity Profile and Final Project
Others
Hands-on Cybersecurity Labs, Cybersecurity Certification, Prep Materials, Post Training Support, Job Referrals, Job Application Support, etc.
Join Our Next Cybersecurity + AI Program
No Tech Degree or Coding Skills Required!



Free Bonuses (worth $2,000)
and more Because MORE is BETTER!
Interview Prep + Q & A scripts
Multiple Resume Samples (including transferable Skills & keywords)
CPE hours
Lifetime access to materials
Continuous coaching and mentoring
Access to Private Support Community
Access to CISM study group
Personalized Career Roadmap
Practicals + Lab
Cybersecurity exam preparation materials
Meet Your Coach
Coach Fola Adegoke
(CISSP, ISO27001:LA, CISA, CDPSE, CSM)
Meet Coach Fola, a trailblazer in the world of cybersecurity, celebrated as one of Canada’s Top 100 Black Women to Watch and a leading figure among Canada’s Top Women in Cybersecurity. Her journey began 12 years ago when she transitioned from an associate at KPMG to a path in cybersecurity—a path encouraged by a perceptive supervisor who recognized her potential.
As an immigrant who secured her first Cybersecurity job within two months, she witnessed other non-IT professionals facing challenges in finding employment. Some struggled due to the need to convert their qualifications to Canadian or US standards, while others resorted to survival jobs or grappled with work-life balance. Motivated by these experiences, she was inspired to assist others in transitioning to this field, leading to the creation of Winfinite Consulting.
Fola has guided over 150 individuals from diverse non-technical backgrounds into fulfilling careers in cybersecurity. Her influence has made her one of the most esteemed black and female career coaches in North America. Her accolades include numerous nominations and awards, and she has been spotlighted in The Guardian & Vanguard Newspapers. Through her programs, drawn from authentic industry experiences, she has launched countless tech enthusiasts into prosperous careers with leading global corporations.


Fortune magazine last year revealed
A staggering 3.4 million shortage of cybersecurity experts.


Cybercrime cost U.S. businesses a whopping $6.9 billion in 2022
Businesses are on the hunt for skilled problem-solvers who can tackle these challenges and they're offering six-figure salaries.


Start Today!
At Winfinite Consulting, we understand the unique challenges you face—whether you’re a new immigrant trying to overcome biases, or someone looking to change careers and unlock your full potential. We equip you with the skills, knowledge, and confidence needed to succeed.
Now, imagine waking up one morning in your DREAM JOB—the kind where you’re a highly paid Cybersecurity professional, surrounded by bright minds. Imagine having a clear ROADMAP to achieve this dream career, regardless of your background.
Our courses are designed not only to help you start getting interviews and landing a job right away but also to empower you to earn the kind of compensation that will elevate your entire lifestyle.
Well, guess what? That dream is closer to reality than you think. Schedule your call today, and let us help you make it happen.


Frequently Asked Questions
What is Cybersecurity and why is it important?
Cybersecurity refers to the systems, technologies, processes, governing policies, and human activity an organization uses to safeguard its digital assets.
It is the practice of protecting computer systems, networks, and sensitive information from unauthorized access, theft, damage, or disruption. This includes protection against malware, hacking, phishing, and other cyber threats to ensure the confidentiality, integrity, and availability of digital information.
GRC stands for Governance, Risk Management, and Compliance in the context of cybersecurity. It's crucial for organizations to effectively manage their IT resources, mitigate risks, and ensure compliance with regulations. It helps protect against cyber threats and ensures that businesses operate securely and within legal boundaries.
Can you provide an overview of the Cybersecurity Launchpad Program?
Our Cybersecurity Launchpad Program is a practical and beginner-friendly program that provides you with hands-on industry experience and job-ready skills. It is suitable for individuals with zero tech experience or no technical degree.
It is a combination of self-paced digital courses and weekly live classes for 10 weeks. Live classes are held on Saturdays from 11 a.m. to 2 p.m. and Mondays from 6 p.m. to 7 p.m. EST
Can a person with no prior IT experience take the program?
Absolutely! Our Cybersecurity Launchpad Program is a practical and beginner-friendly program that provides you with industry experience and job-ready skills. It is suitable for individuals with zero tech experience or no technical degree.
It is designed to accommodate individuals with varying levels of IT experience. Whether you're new to IT or seeking to enhance your skills, our training program is structured to provide valuable insights and knowledge.
The training starts from basic IT concepts and slowly builds up to intermediate and advanced IT concepts.
What tools are used during the Cybersecurity Launchpad training?
Our Cybersecurity training program utilizes various tools, including ServiceNow, Excel, Qualys, Metasploit, Nmap, ZAP and Command Prompt to provide a comprehensive learning experience
Can I pay in installments?
Yes, we offer three payment options:
- Full Payment: The cost is $2500 CAD. This option grants you full access to our digital courses, course content (including resume templates, interview prep resources, exam prep materials), and career support videos. You will also have access to a Career Coach.
- Two-Time Payment: This option allows you to pay in two installments of $1300 each. You'll make a 50% deposit at registration and the remaining balance will be due by week 4 of the program
- Finance Option at 0% interest via Klarna or Affirm: This option allows you to pay multiple times at your convenience at 0% interest rate via our Partners.
How long will I have access to the training materials after the program?
You will have lifetime access to downloadable training materials, 6 months of access to the digital self-paced course and 1 year access to the recorded live classes from the cohort's start date.
What is the typical class size and how is it managed?
We carefully manage class sizes to create an optimal learning environment, ensuring personalized attention, interactive sessions, and effective feedback for all participants.
What do I receive upon completing the program?
Upon completion of the program, you will receive a Completion Certificate with Continuing Professional Education (CPE) hours. Additionally, you will gain practical skills for optimal job performance, access to on-the-job templates and class resources, interview Q&A scripts, resume samples and Job Referrals to support your career development.
How many instructors are involved in the program?
Our program is led by a team of 5 industry expert instructors, each specializing in specific domains of cybersecurity. Their diverse expertise ensures a comprehensive and high-quality learning experience for our students.


Clients Success
This program is for you, if you:
Are committed to learning and practicing new found knowledge.
Demonstrate the willingness to put in necessary efforts to succeed.
Embrace the mindset of excellence and constantly striving for improvement.
Are committed to showing up everyday and fully dedicated to succeed.
Will approach this journey with confidence, fully believing that you will succeed.